Packet Analytics
Project Name: Packet Analytics
Description: Packet Analytics includes understanding Packet.
Both will perform this activity in Real Time so as to resolve many issues like DOS attack, DDOS Attack, Insider Threats, Access Intelligence, Bandwidth Issue and many more.
Author: Rohit D Sadgune
Frequently Asked Question on MOLOCH Packet Analytics
- What is MOLOCH Packet Analytics
- how to use MOLOCH
- How Elasticsearch works with MOLOCH
- How to install MOLOCH
- What is use of Packet Forensics
- Fundamentals of Packet Inspection
- How to configure MOLOCH
- What are different use cases of MOLOCH Packet Analytics
Summary of Content
| ISO / OSI Layer | Packet Inspection | Packet Structure |
| Packet Analytics | Application Traffic Analysis | Host Based Analysis |
ISO OSI Layer
ISO / OSI layer consist of 7 Layers. Each layer adds its own valuable information along with data as unique identification for peer layer.
Each layer needs to add some control information to the data in order to perform its services. This valuable chunk is typically added to the data before it is being given to the lower Layer.
|
Layer |
Header |
| Application | PDU (Protocol Data Units) |
| Presentation | |
| Session | |
| Transport | Segments |
| Network | Packets |
| Data Link | Frames |
| Physical | BITS |
As packets work on Network Layer we will look into the detail of Network Layer Header.
Network Layer Header Components
- Protocol Suite Version
- Type Of Service
- Length Of The Data
- Packet Identifier
- Fragment Number
- Time To Live
- Protocol
- Header Checksum
- Source Network Address
- Destination Network Address
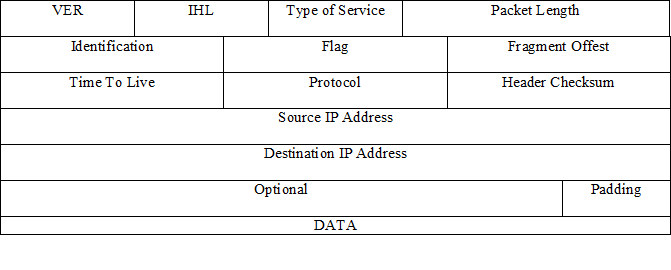
Packet Structure
- VER
- IHL
- Type of Service
- Packet Length
- Identification
- Flag
- Fragment Offest
- Time To Live
- Protocol
- Header Check sum
- Source IP Address
- Destination IP Address
- Optional
- Padding
- DATA
Packet Inspection
Signature Based
- Header Based
- Deep Packet Inspection
Behavior Based
- Statistical Analysis
- Data mining
- Protocol Analysis
Packet Analytics Concepts
- Packet Analytics is the process of capturing the network traffic & performing deep diving analysis to determine what transaction is happening on network.
- Packet Analytics give detail analytical view for activities & communication which is happening or has happened over the network.
- Anomaly Identification
- Traffic analysis can also be done for anomaly detection using network traffic.
- By creating outline of network traffic we can determine host, application & network level of access intelligence.
- Packet Analytics can be used to identify DDOS, DOS, Probbing, MAC Flooding
- Packet Analytics is also used to perform Network Planning, Network Monitoring, Security Analytics
- Network Traffic Forensics includes following aspects :
- Who has done the communication with whom
- When the communication was happened
- Connect of Message
- Length of Message
- Time stamp of communication
- Packet Analytics includes aggregation, decoding & extracting useful information of packets.
- Protocol based packet analytics
- Identification of traffic based on protocols which included source port & destination port.
- We can also create baseline or profile for identification of threats
- Parameter for Packet Analytics
- In Packet Analytics, manner & pattern of communication is more important.
- Analytics is more of analysis of header
- Application based Packet Analytics
- Different application work on different platforms & uses different protocol
- Primary objective is to identify & differentiate such traffic for more analysis
- Differentiating application based on protocol is a wrong adoption of method. Here the contextual analysis fails.
- Packet and protocol based decoding is required when application uses custom ports for communication
- In stateful packet analytics identification & preservation of context is very important.
- Stateful traffic analysis is best way to identify such application based traffic.
- In stateless packet inspection each packet needs to be analyze separately. In stateless packet analysis session, protocol, traffic, IPs needs to be correlated with each other manually. But it is not a true contextual analysis and it may give false positive result.
- Host Base Traffic Analytics
- Identifying the traffic based on IP address
- This method is useful for Host behavior analysis
- Critical patters of traffic needs to be analyzed for any potential threats
- Analyzing the top host which are sending or receiving maximum amount of traffic.
- It is very helpful to understand worms, Malware, Trojans, Botnets and Advance Persistent Threats with respect to contextual analysis of packets.
- Access Intelligence: – Packet Analytics help to provide authorized access to system resources, applications, servers, system operation and functions. We can also perform deep diving analysis by tagging particular system, application or services which are running in the networks
- Packet Analytics is also useful to validate vulnerabilities, exploitation methods, scanning attempts
- Packet Analytics can be used for network monitoring by collecting useful information from different sources and it can be managed & controlled in a contextual manner.
- Packet analytics can also be used for activity profiling using communications of Host, Applications & Different network devices.
Packet Analytics Details
| Sr.No | Packet Analytics Details | URL |
| 1 |
MOLOCH Packet Analytics |
CLICK HERE |
| 2 |
Installation of MOLOCH |
CLICK HERE |
| 3 |
MOLOCH Usage |
CLICK HERE |










